HoneyPoC: The fallout data after I trolled the Internet...
Following on from a pretty funny post, comes some raw data analysis for the data nerds out there. CVE-2020-1350 honeypoc fallout!
To make things easy to quickly scroll through this post to the bits you're interested in, I've made a handy table of contents^.
Introduction
So this week has been an interesting one on the Internet, and what started as a spontaneous project following a patch release(CVE-2020-1350) quickly gained traction becoming one of my most successful GitHub repositories/posts to date. However it has also sparked an accidental research project which in turn has been dubbed a honeypoc which is easier to say than fake-CVE-2020-1350-not-so-malicious-just-a-rick-roll-on-steroids.
Winding back for just a second, if you're reading this thinking what am I on about, you might want to check out the other blog post I made about the fallout. The original post currently has received around half a million reads which is a little insane, so thanks everyone for picking it up and having a gander.
None of this analysis would be possible without the following awesome folks:
Disclaimer: I'm not a data analyst at all. However, here are some of the stats that we were able to collect from the canary tokens that were placed in our POC repository.
So it begins, @ThinkstCanary gave me some JSON on Thursday but a load came in after that so it's some manual parsing combined with JSON to make for some graphs and analysis https://t.co/5khzLBAVFZ pic.twitter.com/kZBH0E8ugO
— Andy Gill (@ZephrFish) July 18, 2020
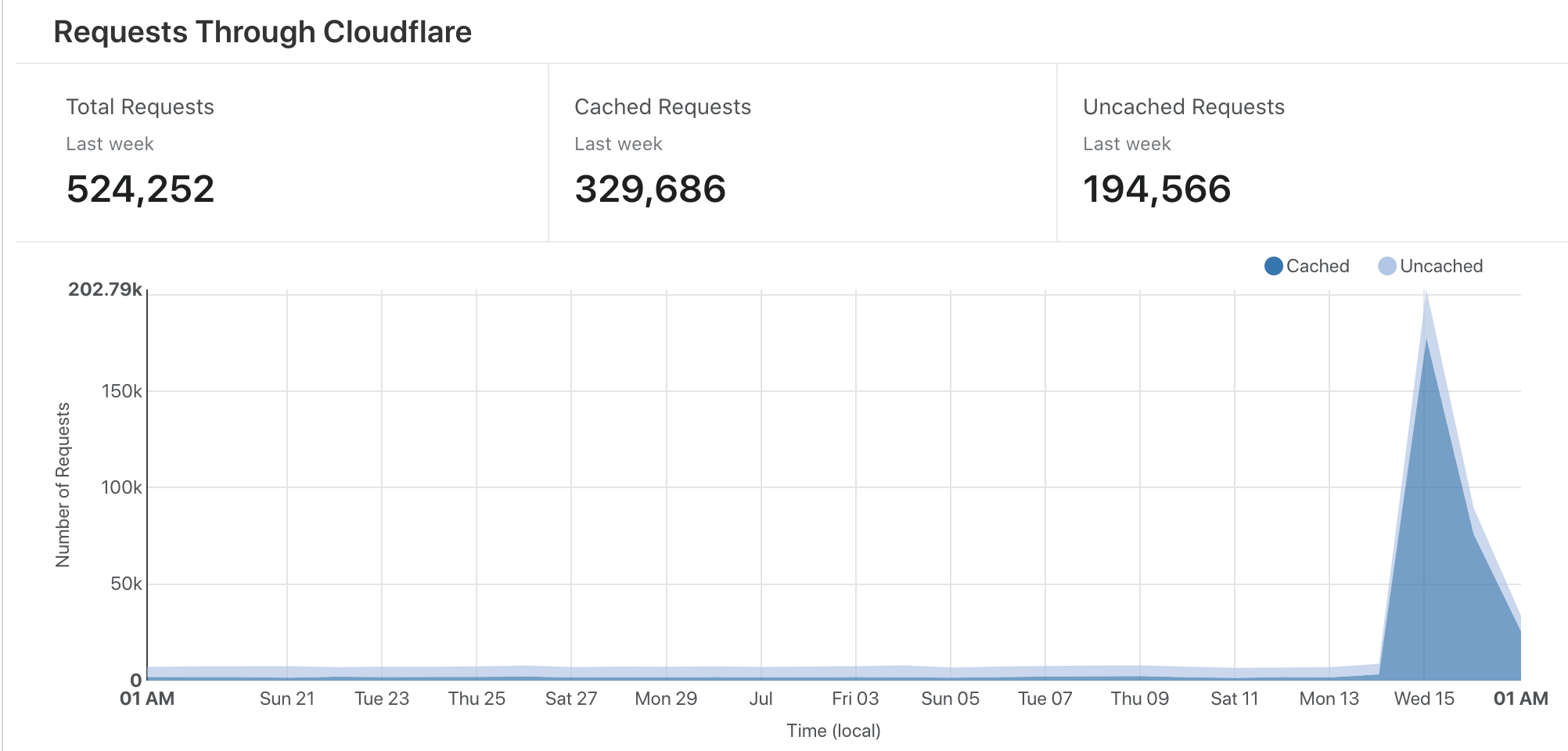
Blog Stats
The graph below is all the requests to the blog in the last few weeks, the peak is the week that the honeypoc was tweeted.
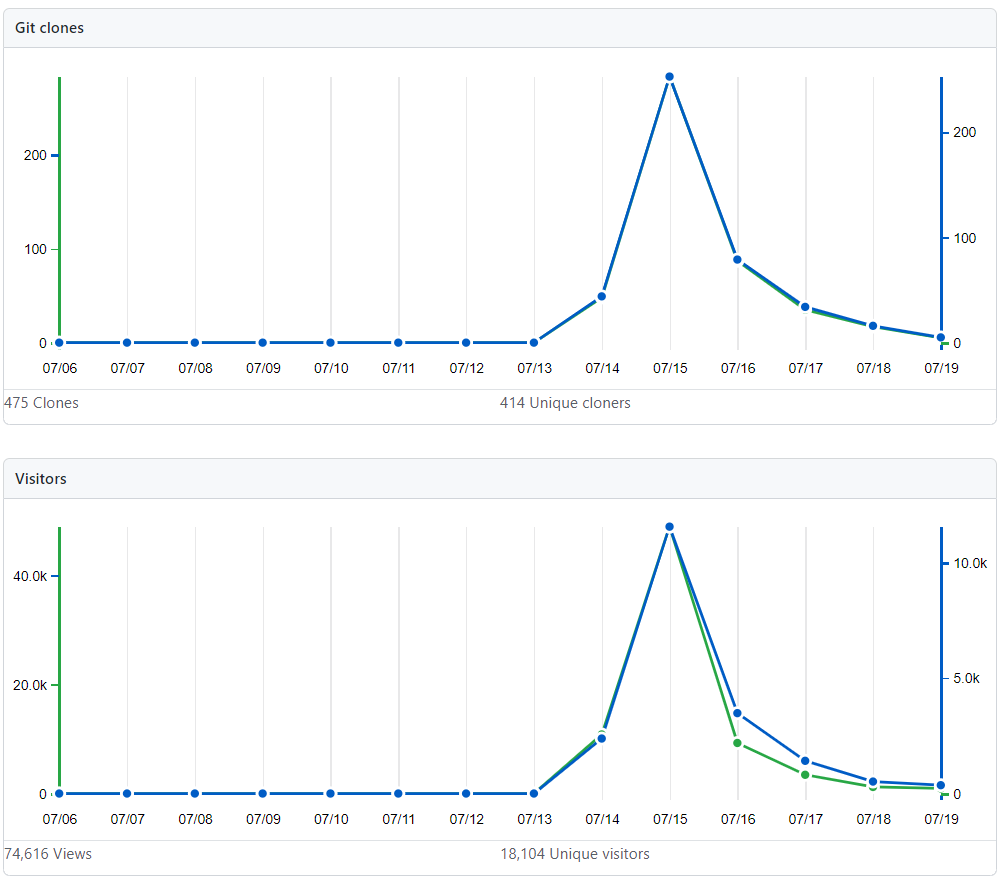
The repository contained four canary tokens, one in the PoC.exe binary, one in the CVE-2020-1350.exe binary, one in the README.PDF and one in the repository README.md. Below are the stats for the repository in terms of clones, views and page visits:
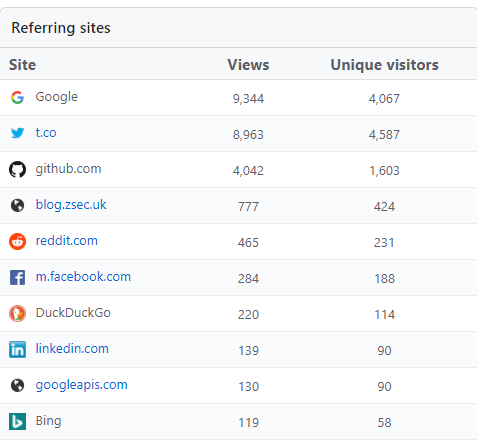
Additional information about the repository includes the sites that were referrers:
Timeline of Events from Original Post
2020-07-14 20:00 GMT+1: Original blog post created by checkpoint
2020-07-14 20:04 GMT+1: PoC Repository first created
2020-07-14 20:09 GMT+1: PoC Tweeted from https://twitter.com/CVE20201350/status/1283116416191934467
2020-07-14 20:33 GMT+1: First retweet of the vuln
2020-07-14 20:48 GMT+1: PoC link hits vulnmon TI feed
2020-07-14 21:06 GMT+1: First canary token hit from IP located in Brussels
2020-07-14 21:29 GMT+1: Tweet started gaining traction
2020-07-14 23:45 GMT+1: TinkerSec's PoC published
2020-07-15 09:09 GMT+1: Cert-IST posted False PoC
2020-07-15 16:10 GMT+1: This blog post posted :-)
2020-07-16 01:50 GMT+1: Stats updated
As we all know data is beautiful, so to start with here is a breakdown of the pings per token, these are unique IPs that pinged back and have been parsed from all of the alert emails.
| Canary Token Source | Total Unique IPs (Execution of Canary) |
|---|---|
| CVE-2020-1350.exe | 622 |
| PoC.exe | 779 |
| README.pdf | 781 |
| Git Repository | 1327 |
It is important that we mention that amount of clicks/executes from exes could be higher but there are some security defences that block canary tokens by blocking the domain or the executable etc.
Geo-IP Breakdown
As that's per token how about a breakdown of per-country and a nice map to follow?
| Country Name | Total Count |
|---|---|
| United States | 326 |
| China | 300 |
| Germany | 89 |
| Hong Kong | 42 |
| Belgium | 39 |
| Japan | 34 |
| Netherlands | 34 |
| Russia | 30 |
| Taiwan | 30 |
| South Korea | 28 |
| Canada | 26 |
| Switzerland | 26 |
| Vietnam | 26 |
| India | 24 |
| Singapore | 24 |
| France | 22 |
| Australia | 20 |
| Iran | 20 |
| Finland | 17 |
| Poland | 16 |
| Spain | 14 |
| United Kingdom | 14 |
| Czechia | 12 |
| Italy | 12 |
| Sweden | 12 |
| Ukraine | 12 |
| Turkey | 8 |
| Austria | 6 |
| Brazil | 6 |
| Bulgaria | 6 |
| Egypt | 4 |
| Hungary | 4 |
| Malaysia | 4 |
| Norway | 4 |
| Philippines | 4 |
| Argentina | 2 |
| Bosnia Herzegovina | 2 |
| Colombia | 2 |
| Estonia | 2 |
| Indonesia | 2 |
| Ireland | 2 |
| Isle of Man | 2 |
| Israel | 2 |
| Moldova | 2 |
| Mongolia | 2 |
| Portugal | 2 |
| Romania | 2 |
| Serbia | 2 |
| South Africa | 2 |
| Thailand | 2 |
| Kazakhstan | 1 |
| Luxembourg | 1 |
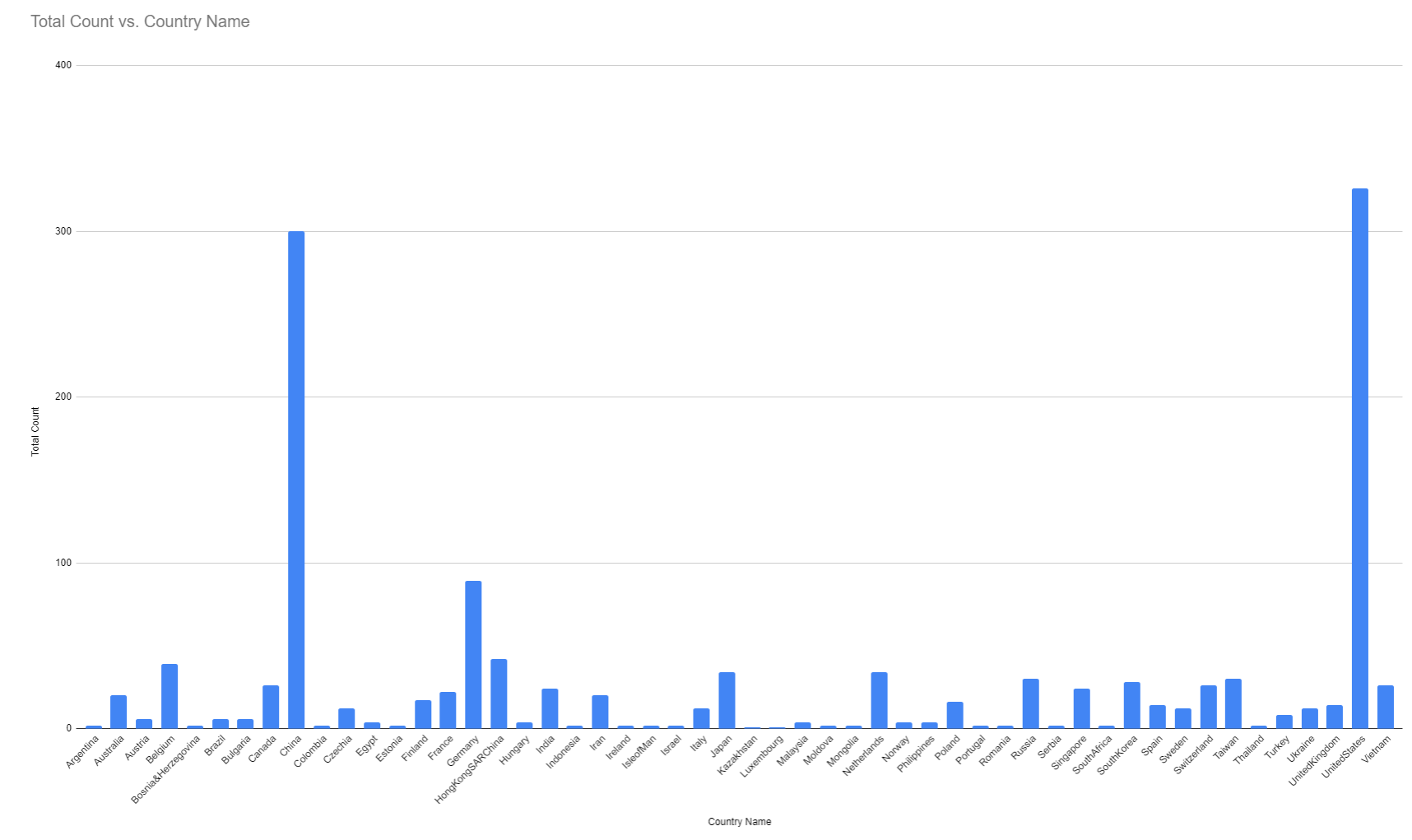
The World as a whole:
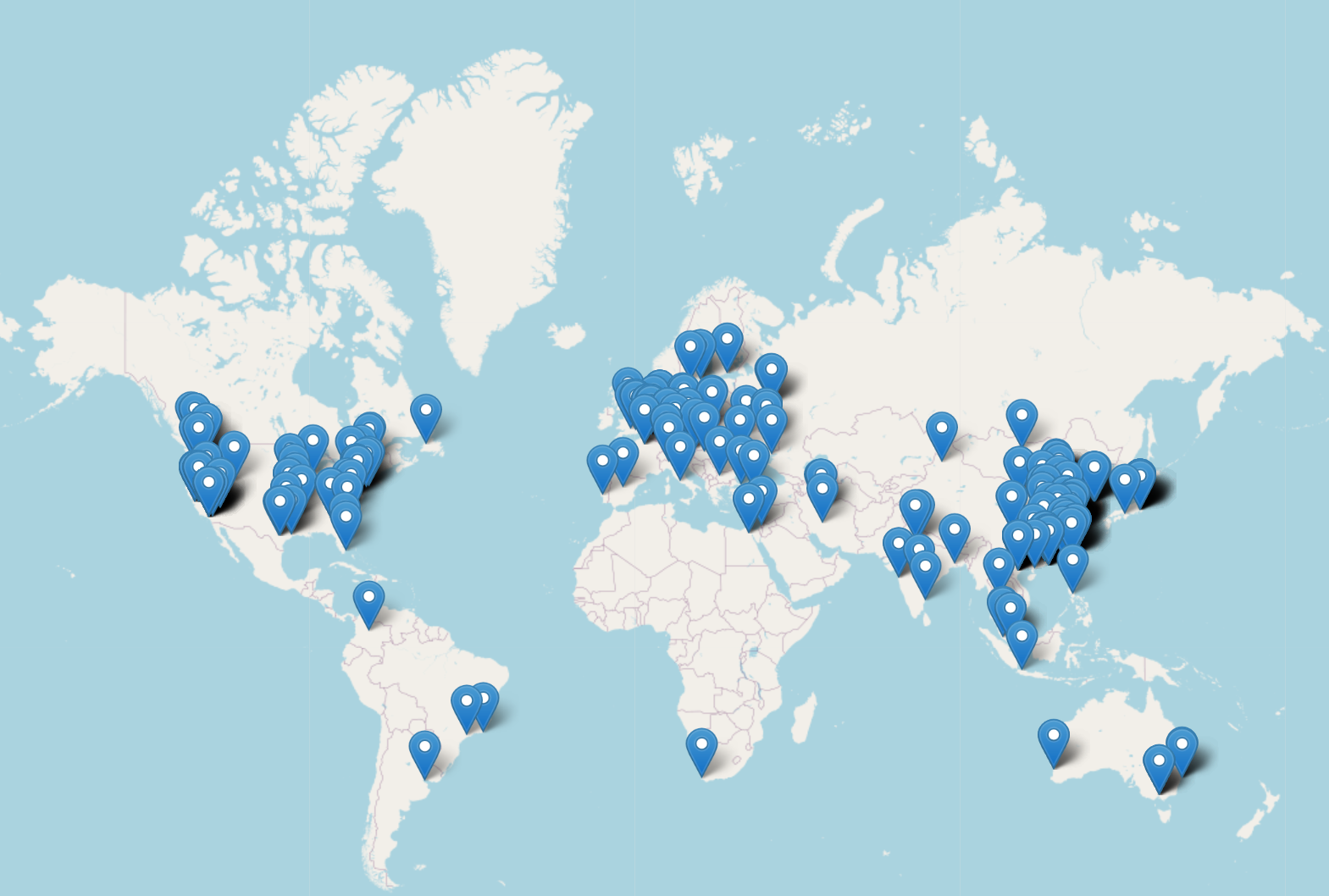
Breakdown per continent:
Europe, Middle East and a little bit of Russia:
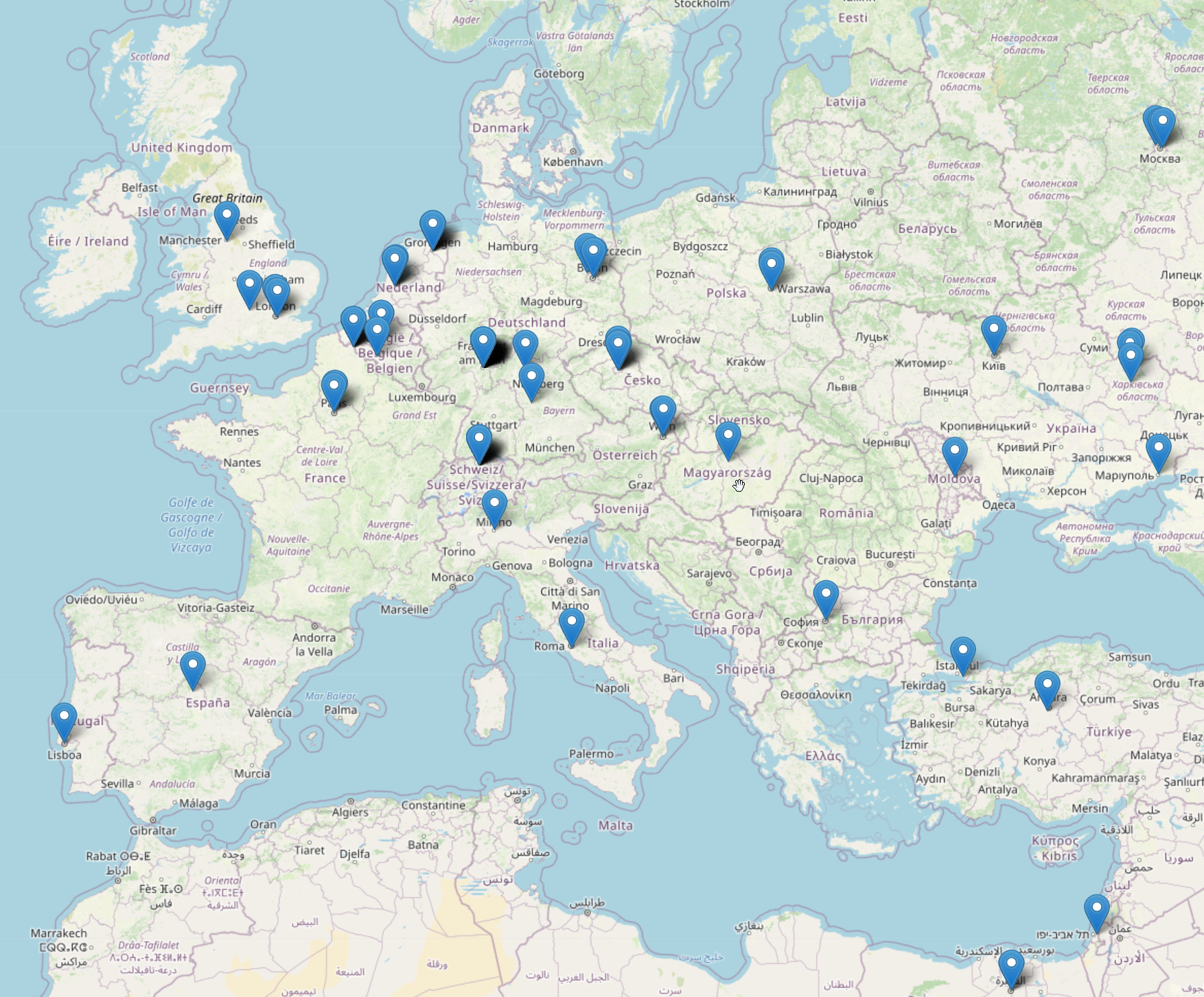
North America:
South America
Africa(oh hey Angus ;) ):
Asia:
Oceania:
In addition to the countries a few other key pieces of info were brought to attention such as 'interesting' IP addresses and other interesting data.
User Agent Breakdown
Onto user agents, we observed 43 unique user agents and many occurrences of each as shown in the table below:
| User Agent |
|---|
| Go-http-client/1.1 , |
| Mozilla/5.0 (Linux; Android 10; SM-N976V) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/83.0.4103.106 Mobile Safari/537.36 , |
| Mozilla/5.0 (Linux; U; Android 4.4.2; zh-cn; GT-I9500 Build/KOT49H) AppleWebKit/537.36 (KHTML, like Gecko)Version/4.0 MQQBrowser/5.0 Mobile Safari/537.36 , |
| Mozilla/5.0 (Macintosh; Intel Mac OS X 10_14_5) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/83.0.4103.61 Safari/537.36 , |
| Mozilla/5.0 (Macintosh; Intel Mac OS X 10_15_5) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/83.0.4103.116 Safari/537.36 , |
| Mozilla/5.0 (Windows NT 10.0; WOW64; Trident/7.0; rv |
| Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/81.0.4044.138 Safari/537.36 , |
| Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/81.0.4044.142 Safari/537.36 , |
| Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/83.0.4103.116 Safari/537.36 Edg/83.0.478.61 , |
| Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/83.0.4103.116 Safari/537.36 , |
| Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/83.0.4103.97 Safari/537.36 , |
| Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/84.0.4147.68 Safari/537.36 Edg/84.0.522.28 , |
| Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/84.0.4147.89 Safari/537.36 , |
| Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv |
| Mozilla/5.0 (Windows NT 10.0; rv |
| Mozilla/5.0 (Windows NT 6.1) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/27.0.1453.93 Safari/537.36 , |
| Mozilla/5.0 (Windows NT 6.1) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/75.0.3770.100 Safari/537.36 , |
| Mozilla/5.0 (Windows NT 6.1; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/72.0.3626.109 Safari/537.36 , |
| Mozilla/5.0 (Windows NT 6.1; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/83.0.4103.116 Safari/537.36 , |
| Mozilla/5.0 (Windows NT 6.1; Win64; x64; rv |
| Mozilla/5.0 (Windows NT 6.1; Win64; x64; rv |
| Mozilla/5.0 (Windows NT 6.1; Win64; x64; rv |
| Mozilla/5.0 (Windows NT 6.2; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/60.0.3112.90 Safari/537.36 , |
| Mozilla/5.0 (Windows NT 6.3; Trident/7.0; rv |
| Mozilla/5.0 (Windows; U; MSIE 9.0; Windows NT 9.0; en-US) AppEngine-Google; (+http |
| Mozilla/5.0 (X11; Linux i686; rv |
| Mozilla/5.0 (X11; Linux x86_64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/49.0.2623.75 Safari/537.36 Google Favicon , |
| Mozilla/5.0 (X11; Linux x86_64; rv |
| Mozilla/5.0 (X11; Ubuntu; Linux x86_64; rv |
| Mozilla/5.0 (compatible) , |
| Mozilla/5.0 (compatible; MSIE 10.0; Windows NT 6.2; WOW64; Trident/6.0) , |
| Mozilla/5.0 (compatible; MSIE 9.0; Windows NT 6.0; Trident/5.0; BOIE9;ENUS) , |
| Mozilla/5.0 (compatible; MSIE 9.0; Windows NT 6.1; WOW64; Trident/5.0) , |
| Mozilla/5.0 (iPhone; CPU iPhone OS 13_5_1 like Mac OS X) AppleWebKit/605.1.15 (KHTML, like Gecko) Version/13.1.1 Mobile/15E148 Safari/604.1 , |
| Opera/9.80 (Windows NT 6.1; Win64; x64) Presto/2.12.388 Version/12.15 , |
| Opera/9.80 (Windows NT 6.1; Win64; x64) Presto/2.12.388 Version/12.16 , |
| Mozilla/5.0 (X11; U; Linux i686; ko-KP; rv: 19.1br) Gecko/20130508 Fedora/1.9.1-2.5.rs3.0 NaenaraBrowser/3.5b4 |
| Python/3.8 aiohttp/3.6.2 , |
| Wget/1.18 (linux-gnu) , |
| Wget/1.20 (mingw32) , |
| curl/7.58.0 , |
| curl/7.69.1 , |
| python-requests/2.22.0 , |
The most common user agent was Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/81.0.4044.138 Safari/537.36 indicating that most users running the binary were on Windows 10.
IP Blocks
There is a lot of analysis that can be done with a big list of IP addresses, one of the suggestions was to look at the most common IP blocks. In total the traffic sources were from 132 unique autonomous system number (ASN) IP blocks. Here's the amount of hits per block!
| ASN Name | Number of Hits |
|---|---|
| AS15169 Google LLC | 128 |
| AS4134 CHINANET-BACKBONE | 35 |
| AS4837 CHINA UNICOM China169 Backbone | 21 |
| AS13335 Cloudflare | 15 |
| AS4808 China Unicom Beijing Province Network | 13 |
| AS4812 China Telecom (Group) | 13 |
| AS8075 Microsoft Corporation | 13 |
| AS37963 Hangzhou Alibaba Advertising Co. | 9 |
| AS9009 M247 Ltd | 8 |
| AS9808 Guangdong Mobile Communication Co.Ltd. | 8 |
| AS4847 China Networks Inter-Exchange | 7 |
| AS4816 China Telecom (Group) | 6 |
| AS3216 PJSC Vimpelcom | 5 |
| AS45090 Shenzhen Tencent Computer Systems Company Limited | 5 |
| AS45102 Alibaba (US) Technology Co. | 5 |
| AS56040 China Mobile communications corporation | 5 |
| AS12695 LLC Digital Network | 4 |
| AS17621 China Unicom Shanghai network | 4 |
| AS4766 Korea Telecom | 4 |
| AS55836 Reliance Jio Infocomm Limited | 4 |
| AS56041 China Mobile communications corporation | 4 |
| AS12880 Information Technology Company (ITC) | 2 |
| AS3257 GTT Communications Inc. | 3 |
| AS54538 PALO ALTO NETWORKS | 3 |
| AS577 Bell Canada | 3 |
| AS7754 McAfee | 3 |
| AS137687 Luoyang | 2 |
| AS138576 CodecCloud (HK) Limited | 2 |
| AS201341 Teso LT UAB | 2 |
| AS206092 Security Firewall Ltd | 2 |
| AS208294 Markus Koch | 2 |
| AS21887 Fiber Logic Inc. | 2 |
| AS24445 Henan Mobile Communications Co. | 2 |
| AS35913 DediPath | 2 |
| AS3786 LG DACOM Corporation | 2 |
| AS55992 Beijing Qihu Technology Company Limited | 2 |
| AS58065 Packet Exchange Limited | 2 |
| AS63888 TISP LIMITED | 2 |
| AS852 TELUS Communications Inc. | 2 |
| AS9644 SK Telecom | 2 |
| AS9814 Beijing FibrLINK Networks Co. | 2 |
| AS11114 Wintek Corporation | 1 |
| AS12329 Telekommunikation Mittleres Ruhrgebiet GmbH | 1 |
| AS12430 VODAFONE ESPANA S.A.U. | 1 |
| AS12576 EE Limited | 1 |
| AS13043 Bayer Business Services GmbH | 1 |
| AS132203 Tencent Building | 1 |
| AS133296 Web Werks India Pvt. Ltd. | 1 |
| AS13414 Twitter Inc. | 1 |
| AS134762 CHINANET Liaoning province Dalian MAN network | 1 |
| AS135330 ADCDATA.COM | 1 |
| AS136192 Xiangyang | 1 |
| AS13768 Aptum Technologies | 1 |
| AS137689 IOT Jiangsu network | 1 |
| AS14061 DigitalOcean | 1 |
| AS16591 Google Fiber Inc. | 1 |
| AS16880 TREND MICRO INCORPORATED | 1 |
| AS17589 GABIA Inc. | 1 |
| AS17638 ASN for TIANJIN Provincial Net of CT | 1 |
| AS18403 The Corporation for Financing & Promoting Technology | 1 |
| AS18434 Fidelity National Information Services | 1 |
| AS198605 AVAST Software s.r.o. | 1 |
| AS201150 Didehban Net Company PJS | 1 |
| AS202425 IP Volume inc | 1 |
| AS202468 Noyan Abr Arvan Co. ( Private Joint Stock) | 1 |
| AS203684 Imen Sanat Novin Alighapoo Private Joint Stock Company | 1 |
| AS204472 Amol Kotkar trading as A K Digital Media | 1 |
| AS20473 Choopa | 1 |
| AS206804 EstNOC OY | 1 |
| AS207400 AAEX NETWORK TECHNOLOGY LTD | 1 |
| AS21859 Zenlayer Inc | 1 |
| AS22616 ZSCALER | 1 |
| AS23576 NBP | 1 |
| AS23693 PT. Telekomunikasi Selular | 1 |
| AS23724 IDC | 1 |
| AS24000 24.hk global BGP | 1 |
| AS24086 Viettel Corporation | 1 |
| AS24444 Shandong Mobile Communication Company Limited | 1 |
| AS24835 Vodafone Data | 1 |
| AS25820 IT7 Networks Inc | 1 |
| AS262287 Maxihost LTDA | 1 |
| AS2856 British Telecommunications PLC | 1 |
| AS28581 Banco Santander (Brasil) S.A. | 1 |
| AS3269 Telecom Italia S.p.A. | 1 |
| AS3301 Telia Company AB | 1 |
| AS33387 DataShack | 1 |
| AS3356 Level 3 Parent | 1 |
| AS36007 Kamatera | 1 |
| AS38631 LINE Corporation | 1 |
| AS39513 TOV ONECOM | 1 |
| AS40028 1651884 Ontario Inc. | 1 |
| AS40676 Psychz Networks | 1 |
| AS43797 The Federal Guard Service of the Russian Federation | 1 |
| AS44244 Iran Cell Service and Communication Company | 1 |
| AS45064 BEIJING ZHONGGUANCUN SOFTWARE PARK DEVELOPMENT CO. | 1 |
| AS45237 Bodicom ISP Ulaanbaatar | 1 |
| AS45382 EHOSTICT | 1 |
| AS45806 Siam Commercial Bank | 1 |
| AS45974 NHN | 1 |
| AS46158 OCM BOCES | 1 |
| AS46887 Lightower Fiber Networks I | 1 |
| AS4713 NTT Communications Corporation | 1 |
| AS47262 Hamara System Tabriz Engineering Company | 1 |
| AS47524 Turksat Uydu Haberlesme ve Kablo TV Isletme A.S. | 1 |
| AS4775 Globe Telecoms | 1 |
| AS49981 WorldStream B.V. | 1 |
| AS51852 Private Layer INC | 1 |
| AS54600 PEG TECH INC | 1 |
| AS5483 Magyar Telekom plc. | 1 |
| AS55286 B2 Net Solutions Inc. | 1 |
| AS55710 201-A | 1 |
| AS56046 China Mobile communications corporation | 1 |
| AS56048 China Mobile Communicaitons Corporation | 1 |
| AS5617 Orange Polska Spolka Akcyjna | 1 |
| AS56402 Dadeh Gostar Asr Novin P.J.S. Co. | 1 |
| AS56466 Pars Fonoun Ofogh Information Technology and Communications Company LTD | 1 |
| AS56526 PC Media Zmijov | 1 |
| AS57858 Inter Connects Inc | 1 |
| AS58563 CHINANET Hubei province network | 1 |
| AS60117 Host Sailor Ltd. | 1 |
| AS63835 CT-HuNan-Changsha-IDC | 1 |
| AS64280 Palo Alto Networks | 1 |
| AS702 MCI Communications Services | 1 |
| AS7385 Allstream Business US | 1 |
| AS7552 Viettel Group | 1 |
| AS8551 Bezeq International-Ltd | 1 |
| AS8886 PGE Systemy S.A. | 1 |
| AS9119 SOFTNET d.o.o. | 1 |
| AS9304 HGC Global Communications Limited | 1 |
| AS9357 NRI SecureTechnologies | 1 |
| AS9534 Binariang Berhad | 1 |
| AS9925 Powerbase DataCenter Services (HK) Ltd. | 1 |
'Interesting' IPs & Hostnames
Out of the list above there are a few that stick out as 'interesting':
- The Federal Guard Service of the Russian Federation (AS43797).
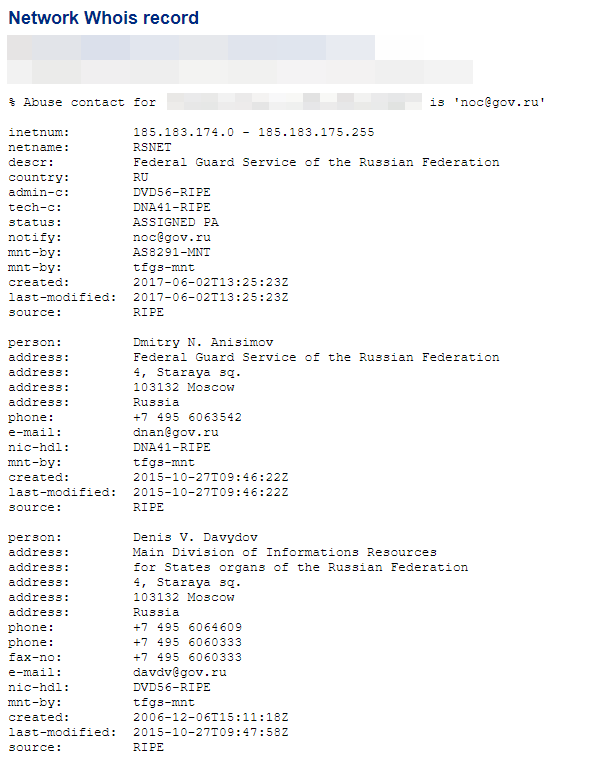
- CHINANET-BACKBONE - China...
- Siam Commercial Bank - Some bank in Thailand!
- AS23028 Team Cymru Inc. - Threat Intel company, didn't pick up the poc and run with it though, so probably just a lookup.
- Some VPN traffic through TOR exit nodes: We've found user agents that link to North Korea (Mozilla/5.0 (X11; U; Linux i686; ko-KP; rv: 19.1br) Gecko/20130508 Fedora/1.9.1-2.5.rs3.0 NaenaraBrowser/3.5b4), Naenara Browser is the DPRK’s version of Firefox that comes built into Red Star OS, the official operating system of North Korea.
There's a lot of security vendors in there too but I assume they're in there for writing signatures etc:
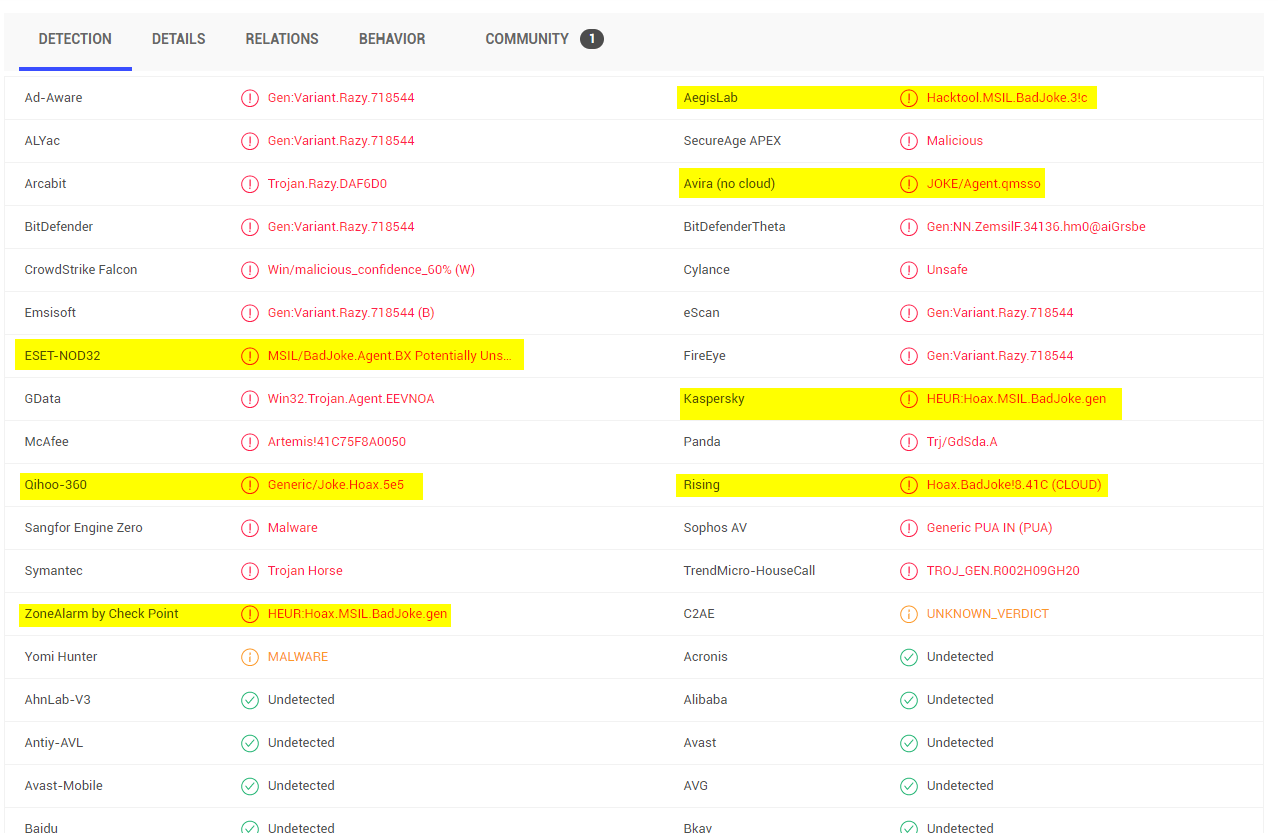
I also ran the IPs found against Alexa top 500 domains, however not many returned anything interesting, the most common domains were AWS and GCP domains.
Remember Folks Rick is Malicious😉
All in all it has been a pretty interesting accidental research project and I can already hear the salty folks who got burned running it 😉. I'll update the post if I get any more interesting info about the IPs in future!




