WTF is Rainbow Teaming?

Alternative Title: 50 Shades of Teams
Red Team, Blue Team, Purple Team, Black Team… Rainbow team? What are all of these things and what do they all mean? Is this a new case of a new found buzzword bingo or do they have a place and a purpose?
The coloured teams are something that is thrown around a lot and while some of them are better known than others I hope to break them down in this post and make it all a little clearer for you, the reader.
Daniel Miessler created the B.A.D triangle; Build Attack Defend which visualises the different teams at a high level:
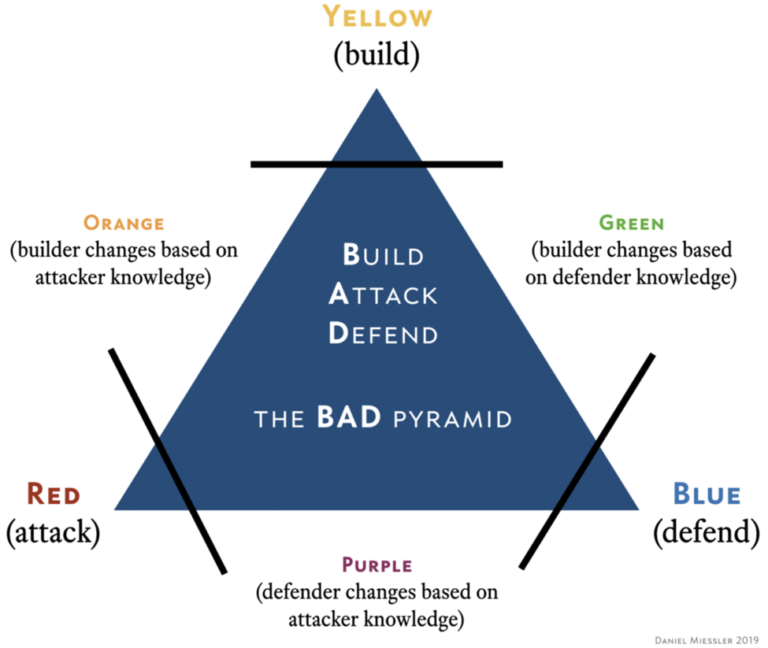
So, rewind a second, what are the different types of teaming, why do they exist and what is their purpose. While some are used and chatted about a lot in the industry others are rarely used, the list below details each colour and the primary role of said team:
- Red Team – Attackers, simulating adversaries and conducting offensive security, the red team’s goal is to simulate threats against an organisation and effectively test the security measures implemented by an organisation.
- Blue Team – Defenders, keeping the network and users secure :-), they have the hardest job arguably. Their job is to protect and defend an organisation’s assets from threats and act on detections.
- Purple Team – Act as a mediator between red and blue they are tasked with boosting the effectiveness of the Red and Blue teams. The purple team add value with insight from attackers but with added incident response and defensive practices to effectively up skill both sides and improve security over all.
- Yellow Team – The general builders, usually software dev or architects responsible for creation of networks, software or implementation of other assets.
- Green Team – Builders who change their design and implementation based on defense knowledge, similar to the orange team however instead of taking cues from the red team, these are drawn from defensive practices.
- Orange Team -Building based on input from attacker knowledge, the orange team is made up of a yellow team but with direct input from a red team mindset, which results in adaptations of implementations based on attacker knowledge.
- Black Team – Usually referred to as physical security assessments, the naming is drawn from black op engagements whereby the teams used to dress in all black to carry out stealth operations. Key features of a black op(eration) are that it is secret and it is not attributable to the organisation carrying it out.
- White Team – The team that establishes the rules of engagement and are usually the employees of the organisation who are undertaking a red or purple team engagement. The white team does not conduct any testing.
The diagram below(courtesy of hackernoon) details how each of the coloured teams are made up based upon the primary base teams of blue, red and yellow:
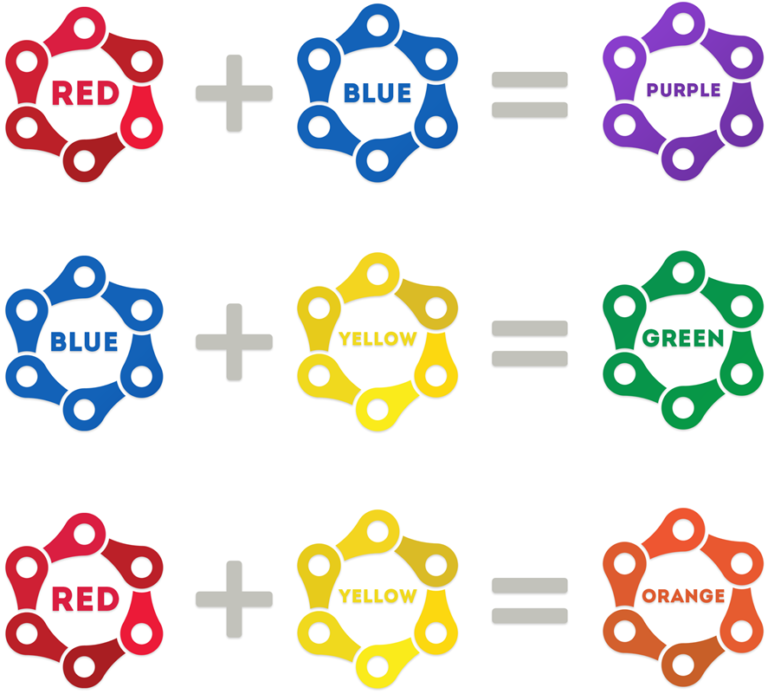
Multi-Colour Teams
Given the overview detailed above I’m going to deep dive into three of the many teams in this post; Red, Blue and Purple. Anyone working in attack-defend areas of security will have likely heard of blue being defensive and red being offensive security, some may have even heard of purple as being a mix of the two. I’ve pulled together this post to try and smash through the nonsense being thrown about describing and selling each as a different thing.
TL;DR The red team attacks and the blue team defends. The purple team mediates between the two offering insight from both a blue and red perspective.
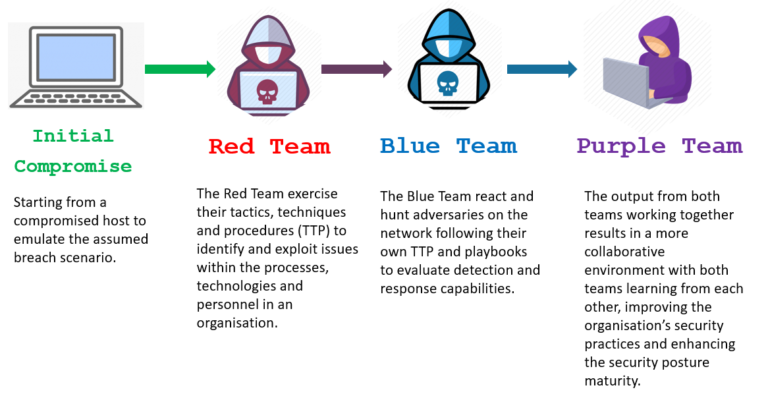
What is a Red Team Engagement?
A red team engagement is an objective-based assessment that requires a holistic view of the organisation from the perspective of an adversary. This assessment process is designed to meet the needs of complex organisations handling a variety of sensitive assets through technical, physical, or process-based means.
The purpose of carrying out a red team assessment is to demonstrate how real world attackers can combine exploits and tactics to achieve their goal. It is an effective way to show that even the most sophisticated technology in the world means very little if an attacker can walk out of the data centre with an un-encrypted hard drive. Instead of relying on a single network appliance to secure sensitive data, it’s better to take a defence in depth approach and continuously improve your people, process, and technology.
Red Teams are brought in by mature organisations to assess their blue team to ensure that, should a real world attack occur, the defensive capabilities are sufficiently tested and prepared.
What is Blue Team?
The blue team are the good folks that often do not get enough praise, they are the real heroes in this story. The blue team are the front line defenders who work at all levels to protect a network from nefarious activity and help to secure businesses day in day out. Their primary role is to act as the varying lines of defence of companies’ networks, similar to the offensive side of security blue teamers come in many flavours.
While I have never worked in blue team roles, I do have a lot of friends who work in the sphere, so my knowledge is second hand from speaking to them and reading for myself. I have however implemented defensive practices in lab environments and written about them before but I am by no means an expert on the subject.
What is Purple Team?
The point with purple-teams being, the collaboration and clear goals of security improvement, education and attacker insight for internal security teams. They do this by integrating the defensive tactics and controls from the blue team with the threats and vulnerabilities found by the red team into a single narrative that maximizes both. Ideally purple shouldn’t be a team at all, but rather a permanent dynamic between red and blue.
Although they share a common goal, red and blue teams are often not aligned or informed with open communications, which leads to businesses not leveraging the full value of their combined teams’ expertise.
Red teams and blue teams should be encouraged to work as a collaborative team, to share insights beyond reporting, with a primary focus on creation of a strong feedback loop to create a more diverse security model, and to look for detection and prevention controls that can realistically be implemented for immediate improvement. The beauty of purple teams is that both sides give insight into similar problems with a different perspective thus collaboration can create effective solutions to complex problems.
Importance of Purple, Red and Blue
While red teaming is lots of fun, I’ve found a new love for bypassing defensive measures then helping folks improve. One could argue the point in a red team is to assess an organisation’s ability to detect and triage a real threat. Part of this is assessing the blue team’s capability as to how different processes kick in to triage and irradiate threats/risks on the network however often this varies depending on the organisation and the maturity of the defensive teams.
There are a few reasons people undertake security testing, the majority of reasons either come down to a requirement from 3rd parties or compliance. However sometimes for a company to take security seriously they need to have been breached or suffered an attack of some sort, and at this point pen testing can be too late. Thus implementing a robust security arm of the business is key.
Red, blue and purple teaming are the way in which an organisation should be addressing their security implementations across the business. If you as a business are relying on an annual pen test and traditional anti-virus to protect your business against threats then it’s already game over. If you’ve done simulated attacks in the past where the measurement of success is if red bypasses x or blue spots y but the engagement is taken no further, then who is learning or gaining value from this?
