ZTH-CH1: From Zero to Technical Hero
This post will take the very core basics and explain them in a series of analogies that are easier to understand if you're completely non-technical or have minimal know-how. I want to make information security and the technicalities more accessible to the masses.

Introduction
I'm just back from a live hacking event hosted by Hackerone in London, UK which was a lot of fun. It's also the reason why this post came to be, I brought my girlfriend along to the event who is not a techie at all but she is really interested in how things work and after seeing how lucrative and exciting bug bounties can be she signalled that she was interested in learning.

Originally this post was going to be one big guide for folks who don't understand or haven't looked at the core technical topics; however, that quickly grew arms and legs. As a result, it will now become a free ebook, with accompanying posts along the way with general hints and tips.
There are always talks of how there aren't enough people in the security industry and that there are many routes into the industry. However, has anyone ever taken a step back, looked at things from a non-technical standpoint, realised it is pretty interesting and wanted to learn more? Sound like something you've thought before? Then this post is for you, if not and you're reading anyway somehow, welcome!
Given that there's already a book out there that explains some bits and pieces about the basics(LTR101), it does assume a bit of technical understanding. If you know what DNS means, or have an understanding of what OSI might mean then jump straight into the book. If those two acronyms mean nothing to you and you are none the wiser, don't worry I've got you covered.
This post will take the very core basics and explain them in a series of analogies that are easier to understand if you're entirely non-technical or have the minimal know-how. I want to make information security and the technicalities more accessible to the masses.
This post will assume nothing and serve as a prequel to my book (LTR101), so if you feel you know it all or some of it well enough skip on. Additionally, if you have any recommendations, please get in touch on Twitter.
If you are reading this and don't see yourself as technical, don't be afraid it's not witchcraft.

All it takes is a bit of Googling(searching the web for the answers), reading & determination. All of the information below will be presented in a relatable manner with analogies that hopefully sync up with common sense, to enable you to understand better how things work and why they work.
Structure
I'm going to explain some fundamental concepts that some people may find easy to understand whereas for others it will just click. So hang on and bear with me, please.
As mentioned above also this tutorial will be split into two sections:
-
Scratching the itch of wanting to learn this stuff
- Following on from general advice, this section will take steps to explain some core technical fundamentals in a relatable way which hopefully you'll understand.
-
General Security Advice
- This section will give the reader some hands-on tips about good security practices to follow in general, to live a more secure life and to become more vigilant about things.
Common Phrases & What They Mean
In the world of technology and security, in general, there are a multitude of different phrases, three letter acronyms and other nonsense chucked about. Before we get started here are a few common phrases I will use throughout and what they mean:
- TL;DR: Too Long Didn't Read, basically a summary of something be this code, an article or general writing. Why am I explaining this here? Well, I might use TL;DR more than once throughout this post to summarise a section at the top making it easier for folks to glance over topics they understand.\
- Hacking: A commonly misunderstood phrase that is closely tied to the connotations of cyber, attacks, malware and other nonsense. However, in truth, it does not mean any of those things; Hacking is finding ways to make something do something it wasn’t originally intended or designed to do. Hacking in and of itself is not a negative thing. Hacking is gaining a deep understanding of how something works and finding ways to manipulate it, and it predates computers.
- Browser/Web Browser: What you use to browse the web on your device, examples include Safari, Firefox, Google Chrome(Chrome), Opera, Iceweasel and many more. Often a browser is referenced when talking about accessing a website, the most common ones are listed above, and you're likely reading this post on one!
- Operating System: This is what your device runs, typically the most common for laptops or desktops is Windows or MacOS and for mobile devices usually IOS or Android. There are other OSes available too, but these are the four most common, Linux/Unix based systems are becoming more common, and I'll explain these later.
- Web/World Wide Web: The World Wide Web, or simply Web, is a way of accessing information over the medium of the Internet. It is an information-sharing model that is built on top of the Internet. The Web is just one of the ways that information can be disseminated over the Internet. The Internet, not the Web, is also used for email, instant messaging, file transfer(download and upload) and other things too. So the Web is just a portion of the Internet, albeit a large part, but the two terms are not synonymous and should not be confused.
- Internet: You will probably be reading this on the Internet but do you know what it is? Well, in short, the Internet is like a gigantic library with books on every subject imaginable, and using this analogy the websites you visit are the books you check-out of the library.
- WiFi: For a lot of people, when I say WiFi they will automatically think that WIFI IS THE INTERNET. Sorry to say it but they are WRONG! WiFi or wireless access facilitates accessing the Internet wirelessly, i.e. not running around with a cable plugged into the wall. It is important to note that it is not only used for accessing the Internet, it can also be used for devices to communicate with one another wirelessly within a particular area.
Logical Thinking
Starting off on a non-technology standpoint. One of the key points often overlooked is logical thinking. If I do an action what is the likely reaction, while this applies to all aspects of life it is also closely tied to security and often technology in general.
This lesson is about how to learn – a critical skillset to have. Hacking, in reality, is a creative process that is based more on lifestyle than teaching. I can't teach you every possible topic that you need to know, but I can help you recognise what you need to learn.
This is also true due to the constant advances in the field of technology and specifically security. What I teach today may not be relevant tomorrow. It is much better for you to embrace the hacker mindset and the learning habits, which are probably the most vital part and will separate you from mere muggles(a person who is not conversant with a particular activity or skill.)
Think of this scenario, if I am using a shopping website and manage to set the price to £0.00 or even a negative value -£1,000,000. What happens? Well in a broken situation the site might permit you to gain the item for free! Or even worse(I've seen it before) credit your account with the negative value!
Understanding How a Computer Works
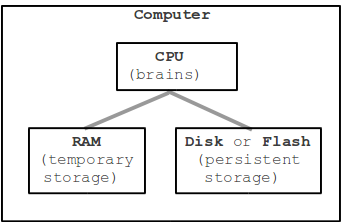
TL;DR: A computer uses the core components to process information, be that browsing the web with a browser, playing music, watching media or writing out documents.
For starters technically, I'm going to explain an analogy as to how a computer works, some key points you might not be aware of and why they're essential.
In the modern era we're living in, the way in which a computer was described to me when I was learning is a lot different now. A computer can be your smartphone, a laptop, desktop or anything these days. However, for this explanation, I'm going to talk about a desktop or notebook and the insides of it(also known as components).
Thanks to Paul Stewart for this analogy. In a computer there are three main components; Hard Drive, Memory also referred to as RAM and a CPU also known as a processor. Imagine these as the following items:
- Filing cabinet = Hard Drive
- Desk = RAM
- You = CPU
You will work a lot faster if you bring the files out of the cabinet and work with it on your desk. This is what a computer does. It can work with the information on the hard drive, but it will be a lot slower. If you have a bigger desk (more RAM/memory), You can get more work done, but only if you (CPU/processor) is working as efficient as possible.
Core Topics
Over the next few posts, I aim to explain the different areas you'll want to look into and learn about to get a better understanding of the technicalities. I believe that anyone can become technical if they are willing to learn.
So some core topics that you might want to have a google of but don't worry; I plan to explain them too in later posts!
- HTTP Protocol Basics: What is a protocol, how does it tie into the Internet/web and why is it important?
- How DNS Works/How the Internet Works?
- Principles of System interaction & assumed boundaries - aka how do I mess with it, what is it supposed to do
- Use and make before you break it!
- Troubleshooting/Debugging
- Other Areas of Interest that can be useful Lockpicking/Social Engineering)
- How to Use Windows & Linux - Beyond the GUI(Graphical User Interface)
- Networks: Building on Operating systems we'll learn about Programming/Coding and some basics of how networks work.
- The concept of different ways to look at a problem.
I hope to cover many more topics too, as the plan is to put this into an ebook, not everything will be covered at once in one post! Hopefully, the post above is enough to get you started and start to get your feet wet :-).
If you liked this post there is a second and third chapter here:
Second
Third
